Safeguard customer data with certified controls and proactive security measures.
SOC 2
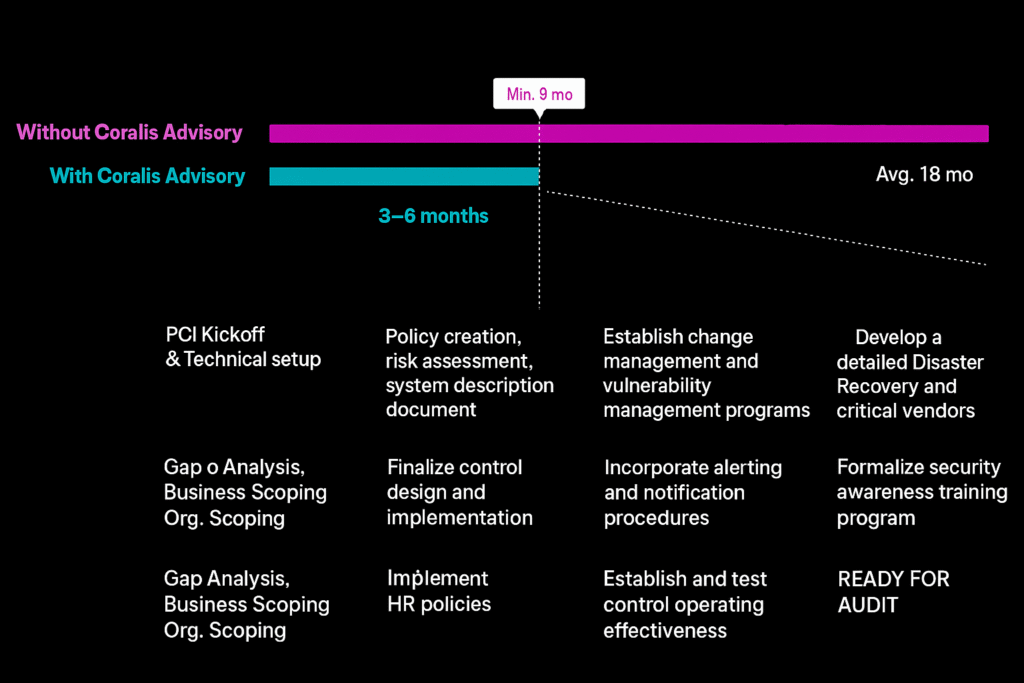
As the most widely recognized cybersecurity framework in the U.S., SOC 2 certification has become a fundamental requirement for companies scaling their enterprise customer base. Audited reports demonstrate your security commitment and are routinely requested during vendor evaluations with established organizations.
Overview
SOC 2 evaluates five critical security domains, with Security as the mandatory baseline and four optional criteria tailored to your business requirements:
Security:
Protection against unauthorized data access, system breaches, or malicious alteration of information assets.
Availability:
Maintenance of operational uptime and reliable access to systems for authorized users and customers.
Confidentiality:
Enforcement of strict access controls for sensitive data through encryption and permission structures.
Processing Integrity:
Validation of accurate, complete, and authorized data handling throughout all system workflows.
Privacy:
Compliance with data collection, retention, and disclosure policies for personal information.
Strategic Implementation Guidance
While Security forms the essential foundation, selecting additional criteria should reflect your:
Data types processed (PII, PHI, financial)
Cloud architecture complexity
Customer and regulatory expectations
Risk management priorities
Why This Matters
Enterprise clients increasingly demand specific criteria combinations – we help you optimize scope for both compliance efficiency and business growth.

Why Clients Work with Us
Customized plans that scale with your business lifecycle
Beyond managed services – we modernize your security operations
Compliance
Catalyst
Fast-Track Compliance for SOC 2, HIPAA & ISO 27001
✔ Single-framework compliance
✔ Rapid audit readiness
✔ US-based compliance team
✔ Customized policies
✔ Auditor management
✔ Hands-on GRC management
✔ Risk assessments & gap analysis
✔ Trust Center configuration
✔ Sales & infosec support
✔ Partner network access
Add-ons available
+ Penetration Testing
+ Internal Audit
+ Managed Vulnerability Scanning
+ Additional Frameworks
Timeline: 3-12 months
Begins at
$5K/MO
adjusts based on number of framework
Customers include
Series Seed – Series B
Continuum
Continuous audit readiness for SOC 2, ISO 27001, and HIPAA
✔ Single-framework compliance
✔ US-based compliance team
✔ Hands-on GRC tool management
✔ Trust Center Maintenance
✔ Security Questionnaires
✔ Sales & infosec support
✔ Partner network access
Add-ons available
+ Penetration Testing
+ Internal Audit
+ Managed Vulnerability Scanning
+ Additional Frameworks
Timeline: Annual
Begins at
$5K/MO
$1K/mo per 50 employees thereafter
Customers include
Companies that completed catalyst
Cybersecurity
Aegis
Achieve best-in-class security and privacy programs
• Multi-framework compliance
• CISO support or replacement
• Technical design enhancements
• Cloud security assessments
• Security questionnaires
• Incident response
• M&A diligence
• Vendor diligence
• Pentesting
• Vulnerability Management
• 50+ other services
Timeline: Multiyear
Begins at
$7K/MO
adjusts based on selected services
Customers include